AppiCryptWeb
Cryptographic Runtime Attestation for
Web Applications
Web Applications
Every request is cryptographically bound to a verified, untampered browser runtime - stopping abuse before it reaches your backend.
.png)
.png)
.png)

AppiCryptWeb changes the game
Modern web applications face increasingly sophisticated threats - from bot-driven abuse and automated scraping to runtime tampering and reverse engineering. Traditional defenses like CAPTCHAs, IP blocking, or cookie-based controls either fail against these sophisticated tactics or frustrate legitimate users.
It’s a WebAssembly-based, in-browser security agent that attaches a cryptographically protected proof - a “cryptogram” - to every API call. This cryptogram represents the integrity of the browser runtime, the state of the device, and the legitimacy of the request itself.
Backends and edge gateways can then validate requests in real time, ensuring they originate from authentic, untampered browsers.
Request Demo


How AppiCryptWeb Works
At the core of AppiCryptWeb is a dual-agent architecture:
Generates a signed cryptogram per API request containing browser fingerprint, threat flags, and a caller-provided nonce bound to that specific call.
Verifies signatures, validates freshness and nonce binding, extracts the browser fingerprint and threat data, computes a risk score, and returns detailed assessment context for customer decision logic.
The two agents communicate over a secure message channel, isolating sensitive logic from synchronous tampering attempts
A lightweight magic file bootstraps the system by delivering the necessary encryption material, policy configuration, and key identifiers. Developers initialize it once per app load:
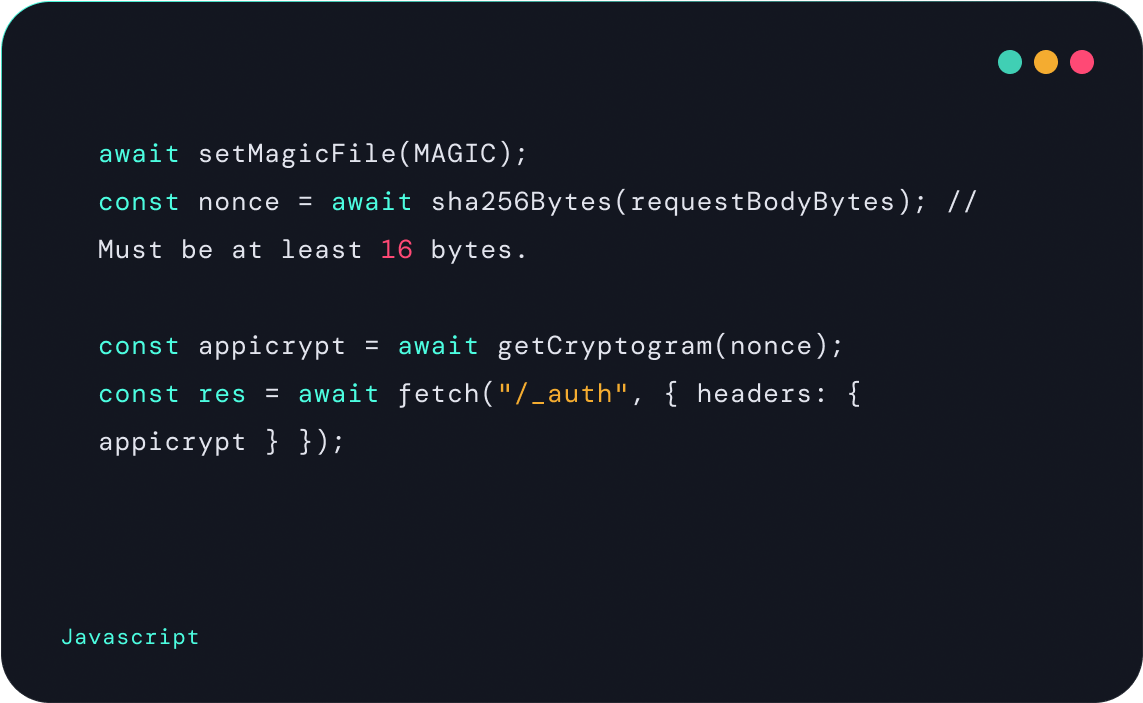
Cryptogram: Proof with Every Request
Each outgoing API call is bound to a per-request cryptogram, which includes

Self-integrity of the WebAssembly modules

Device identity (privacy-preserving browser fingerprint)

Request provenance (nonce + timestamp)

Threat check results (tampering, presence of debugger/DevTools - potential reverse engineering, bot - automation frameworks, incognito mode)
Cryptograms are encrypted and signed using a keypair aligned with the customer’s configuration. The server decrypts, verifies, and enforces policy thresholds before authorizing the request. Failed or tampered states yield 401 (missing) or 403 (invalid) responses.
Security Model Highlights
Together, these mechanisms significantly raise the cost of bypass for attackers, even those with full access to the client environment.
Deployment
AppiCryptWeb is designed to work seamlessly at the edge or within existing backend flows:
If validation succeeds, the request is forwarded to the backend with context and nonce headers, enabling fine-grained risk assessment and decision-making.


Benefits Over Traditional Controls
Privacy-preserving identity
Provides a stable browser fingerprint without cookies or invasive tracking.
Request-level assurance
Every call carries a cryptographic proof of runtime health.
Replay resistance
Every proof is tied to a unique nonce and timestamp, making it useless for replays.
Built for fraud prevention
No reliance on CAPTCHAs or brittle heuristics. Detects tampering, automation frameworks, private/incognito mode, and open developer tools - all in real time.
Minimal integration
Just two frontend calls and one backend validation step.
Edge-ready integration
Works seamlessly with NGINX, Cloudflare Workers, AWS API Gateway, and other modern infrastructure.
-
API Key
Basic CAPTCHA
Modern CAPTCHA (reCAPTCHA, hCaptcha)
AppiCryptWeb
Assurance per request
🔑 One-time check, can be shared/abused
🙅 Manual proof user is human, not request-level
🤏 Score-based, heuristic, not request-bound
✅ Cryptographic proof attached to every request
Identity
🔓 Static string, easily stolen
❌ No device/session continuity
❌ Cookie/session tracking, privacy trade-offs
✅ Privacy-preserving browser fingerprint, cookie-free
Replay resistance
❌ None — stolen key works forever
❌ CAPTCHA once passed, token can be reused
❌ Token reuse possible, depends on heuristics
✅ Each cryptogram bound to unique nonce + timestamp
Fraud prevention strength
⚠️ Weak — easily scripted or stolen
⚠️ Bots can solve or outsource cheaply
⚠️ Bots can bypass with farms or AI
💪 Runtime integrity checks, tamper detection, bot signals
User experience
✅ Invisible, no friction
❌ Interruptive & frustrating
⚠️ Background scoring, sometimes challenges
✅ Transparent to users, no challenges
Integration effort
✅ Minimal
⚠️ Client-side widget, server validation
⚠️ SDK integration + tuning
✅ SDK integration - One frontend call, one backend check
Supported Platforms

AppiCryptWeb delivers cryptographic runtime attestation for the web, enabling businesses to enforce precise authorization, detect threats in real time, and stop abuse at scale - all while preserving user experience.
What Do You Get with AppiCryptWeb?

Comprehensive API protection against
Bots & automation: credential stuffing, scalping, user enumeration, DDoS, AI agent traffic
Fraud & tampering: session hijacking, transaction manipulation, IDOR (Insecure Direct Object Reference) exploits
Data abuse: web API scraping, competitor spying, unwanted traffic
Business & revenue abuse: copyright enforcement, ad revenue protection, prevention of scraping-driven losses
Fraud & tampering: session hijacking, transaction manipulation, IDOR (Insecure Direct Object Reference) exploits
Data abuse: web API scraping, competitor spying, unwanted traffic
Business & revenue abuse: copyright enforcement, ad revenue protection, prevention of scraping-driven losses

Enforced runtime integrity
without degrading UX

Cryptographically verifiable
per-request proof

Seamless integration
with modern edge infrastructure

Privacy-preserving identity
beyond cookies
By binding each request to a verifiable cryptogram, AppiCryptWeb gives defenders what traditional web controls cannot: per-request proof of authenticity, integrity, and runtime security.





